PLMN's need a higher level of protection than traditional telecommunication networks. Therefore, to protect GSM systems, the following security functions have been defined:
• Subscriber authentication:
By performing authentication, the network ensures that no unauthorized users can access the network, including those that are attempting to impersonate others.
• Radio information ciphering:
The information sent between the network and an MS is ciphered. An MS can only decipher information intended for itself.
• Mobile equipment identification:
Because the subscriber and equipment are separate in GSM, it is necessary to have a separate authentication process for the MS equipment. This ensures, e.g. that a mobile terminal, which has been stolen, is not able to access the network.
• Subscriber identity confidentiality:
During communication with an MS over a radio link, it is desirable that the real identity (IMSI) of the MS is not always transmitted. Instead a temporary identity (TMSI) can be used. This helps to avoid subscription fraud. The AUC and EIR are involved in the first three of the above features, while the last is handled by MSC/VLRs.
AUC FUNCTIONS
The primary function of an AUC is to provide information, which is then used by an MSC/VLR to perform subscriber authentication and to, establish ciphering procedures on the radio link between the network and MS’s.
The information provided is called a triplet and consists of:
1. A non predictable RANDom number (RAND)
2. A Signed RESponse (SRES)
3. A ciphering Key (Kc)
Provision of Triplets
At subscription time, each subscriber is assigned a subscriber authentication Key (Ki). Ki is stored in the AUC along with the subscriber’s IMSI. Both are used in the process of providing a triplet. The same Ki and IMSI are also stored in the SIM. In an AUC the following steps are carried out to produce one triplet:
1. A non-predictable random number, RAND, is generated
2. RAND and Ki are used to calculate SRES and Kc, using two different algorithms, A3 and A8 respectively
3. RAND, SRES and Kc are delivered together to the HLR as a triplet

Provision of triplets
Authentication Procedure
1. The MSC/VLR transmits the RAND to the MS.
2. The MS computes the signature SRES using RAND and the subscriber authentication key (Ki) through the A3 algorithm.
3. The MS computes the Kc by using Ki and RAND through A8 algorithm. Kc will thereafter be used for ciphering and deciphering in MS.
4. The signature SRES is sent back to MSC/VLR, which performs authentication, by checking whether, the SRES from the MS and the SRES from the AUC match. If so, the subscriber is permitted to use the network. If not, the subscriber is barred from network access.

Authentication procedure
Authentication can by operator’s choice be performed during:
• Each registration
• Each call setup attempt
• Location updating
• Before supplementary service activation and deactivation
There can be exceptions for subscribers belonging to other PLMN’s.
Ciphering Procedure
Confidentiality means that user information and signaling exchanged between BTS’s and MS’s is not disclosed to unauthorized individuals, entities or processes. A ciphering sequence is produced using Kc and the TDMA frame number as inputs in the encryption algorithm A5. The purpose of this is to ensure privacy concerning user information (speech and data) as well as user related signaling elements. In order to test the ciphering procedure some sample of information must be used. For this purpose the actual ciphering mode command (M) is used.
1. M and Kc are sent from the MSC/VLR to the BTS.
2. M is forwarded to the MS.
3. M is encrypted using Kc (calculated earlier with SRES in the authentication procedure) and the TDMA frame number which are fed through the encryption algorithm, A5.
4. The encrypted message is sent to the BTS.
5. Encrypted M is decrypted in the BTS using Kc, the TDMA frame number and the decryption algorithm, A5.
6. If the decryption of M was successful, the ciphering mode completed message is sent to the MSC. All information over the air interface is ciphered from this point on.

Ciphering procedure
EIR FUNCTIONS
Equipment Identification Procedure
The equipment identification procedure uses the identity of the equipment itself (IMEI) to ensure that the MS terminal equipment is valid.
1. The MSC/VLR requests the IMEI from the MS.
2. MS sends IMEI to MSC.
3. MSC/VLR sends IMEI to EIR.
4. On reception of IMEI, the EIR examines three lists:
– A white list containing all number series of all equipment identities that have been allocated in the different participating GSM countries.
– A black list containing all equipment identities that has been barred.
– A gray list (on operator level) containing faulty or non - approved mobile equipment.
5. The result is sent to MSC/VLR, which then decides whether or not to allow network access for the terminal equipment.

Equipment identification
The decision to identify equipment remains with individual operators. GSM specifications recommend identification for each attempted call set-up.
AUC AND EIR IMPLEMENTATION
In a GSM network the AUC is connected directly to a HLR. The EIR is connected to an MSC/VLR. In some GSM systems the AUC may be implemented on either AXE or Unix (from Sema Group). The EIR is implemented on a Unix platform from Sema Group. If implemented on AXE, the most common configuration for an AUC is integrated with a HLR as an AUC/HLR node. This reduces the signal processing requirements of both. The AUC is implemented using the AUC Application Module (AUCAM). The most common implementation is a Unix-based AUC/EIR node, which provides the following benefits to the operator:
• AUC and EIR processing is physically separated from the switching function in the MSC. This provides better network planning flexibility when the network needs to be expanded.
• The common platform is based on standard industry computer hardware (HW) and software (SW).
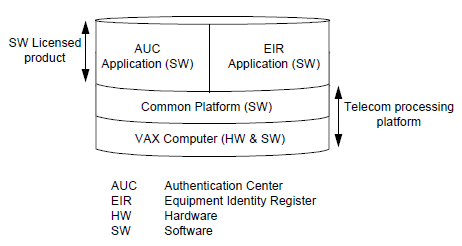
AUC/EIR product structure
Telecom Signaling Penetration Testing ensures the robustness of communication networks. By probing vulnerabilities in signaling protocols, this essential cybersecurity process helps safeguard against potential threats, ensuring uninterrupted and secure telecommunication services. Safeguard your telecom infrastructure with precise testing services experts penetration testing services for enhanced reliability and peace of mind.
ReplyDelete